UKCSC specialisms mapped to SFIA and CyBOK
The UK Cyber Security Council’s 15 specialisms define the domains of cyber security practice, while SFIA provides a practical framework to make them usable in organisations. Together, they can form a powerful, integrated framework.
This page incorporates material developed by the UK Cyber Security Council. Authorship by the Council and identified contributors is acknowledged in line with their publication terms.
The UK Cyber Security Council (UKCSC) Cyber Career Framework is a tool that provides guidance on career pathways in cybersecurity. It outlines 15 specialisms within the industry and offers details on their typical responsibilities, required skills, knowledge, and potential salary ranges. The framework is designed to help both new and existing professionals plan a flexible career route within the sector, not a rigid, one-size-fits-all standard
From specialisms to roles: Applying SFIA skills helps translate each specialism into skills-based role profiles, with defined skills and levels of responsibility. For example, “Secure operations” becomes roles ranging from entry-level, to analyst (SFIA Level 3–4) to managers (SFIA Level 5-6), each with clear requirements. This helps employers turns the Council’s specialisms into skills-based job descriptions, team structures, career paths and training plans.
Career pathways: By applying SFIA’s seven levels of responsibility, each specialism gains a structured career path within and between the specialisms. Professionals can see how to progress from entry level through advanced roles, with SFIA describing the competencies needed at each stage.
Flexibility for employers: Organisations can tailor the framework to their context. Smaller firms may combine specialisms into hybrid roles, while larger organisations may define highly specialised roles — both aligned to the same reference points.
Knowledge to practice: The UKCSC framework has linked the specialisms ton CyBOK’s 21 knowledge areas. SFIA adds the practical layer by linking them to competencies. This helps to translate CyBOK’s conceptual content into workplace practice. Mapping training to CyBOK and SFIA skill and level descriptions together provide targeted development paths.
Professional standards: By combining UKCSC and SFIA, cyber roles can be benchmarked nationally and recognised internationally — supporting professionalisation, workforce mobility, and career-long development.
On this page:
- About the SFIA Framework and the SFIA Foundation
- SFIA Levels of Responsibility
- Diagrams and illustrations
- Illustration of career levels in the cyber security specialisms
- Illustrative career paths for the UKCSC specialisms
- Applying SFIA skills to cyber security focus areas
- Combining skills frameworks and role frameworks for cyber security - NICE work roles, UKCSC Specialisms, ENISA
- CyBOK and SFIA in professional working environment
- SFIA and CyBOK mappings for the 15 UKCSC Specialisms
Structure and content of the SFIA Framework
- Seven levels of responsibility – a progression from following instructions (Level 1) to setting strategy (Level 7).
- Over 140 professional skills – covering not only cybersecurity but also business, data, digital, and organisational skills that cyber roles depend on.
- Also includes detailed definitions of business skills/behavioural factors such as communication, decision-making, collaboration, leadership, problem-solving
- Task/activity/competency orientation – skills are described as tasks and outcomes at each level, not just as knowledge statements.
- Reusability across contexts – the same SFIA skill can apply in cyber, software, data, or business settings, making cross-domain mobility clear. This supports secure-by-design responsibilities.
- Integration with knowledge; CyBOK = knowledge, SFIA = competency; they reinforce each other rather than duplicate.
SFIA Foundation and community
- Global adoption – SFIA is used in 200+ countries, with cyber applications in the UK, US, Canada, Australia, NZ and beyond.
- Trusted governance – stewarded by the not-for-profit SFIA Foundation, with updates driven by a design authority and international consultation.
- Diverse contributors – community includes governments, universities, professional bodies, employers, and practitioners.
- Open and accessible – free for individuals and most employers, with translations into 11 languages and supporting resources.
- Practical support – guidance notes, example role profiles, mappings to standards and other frameworks
- Progressive (Building on the previous level's requirements),
- Distinct (Clearly differentiated from adjacent levels), and
- Consistent (Using uniform criteria across all skills).
The levels are characterised by specific behaviours, values, knowledge and characteristics that indicate an individual's operational capability at that level. The concise essence statements provide a distilled view of the unique characteristics of each level. They help users easily distinguish between levels and understand progression without needing to dive into detailed descriptions.
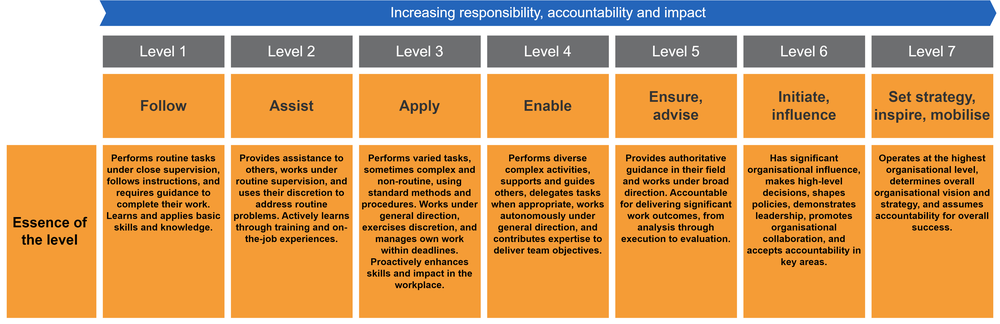
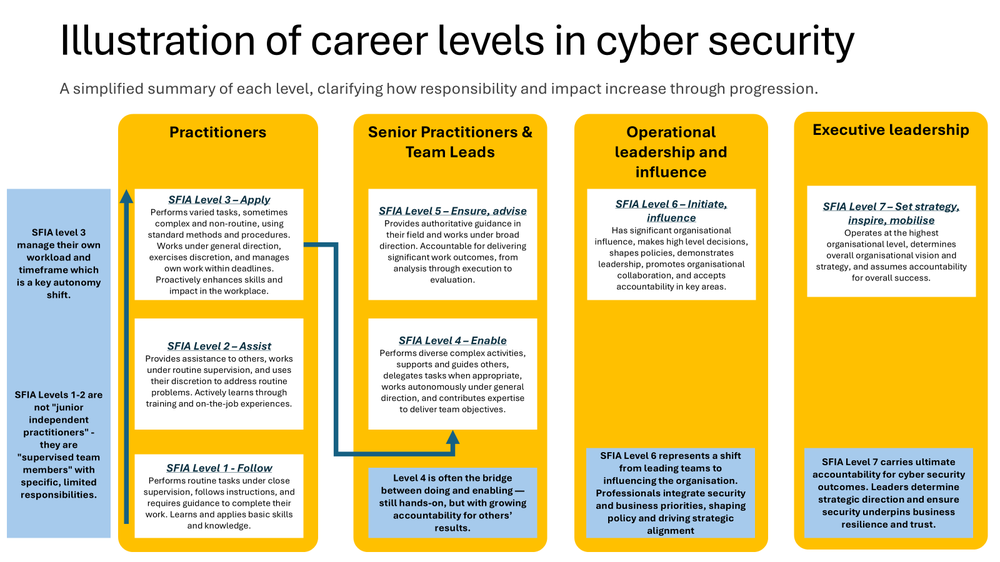
We can apply the SFIA levels to typical career levels found in the cyber security domain.
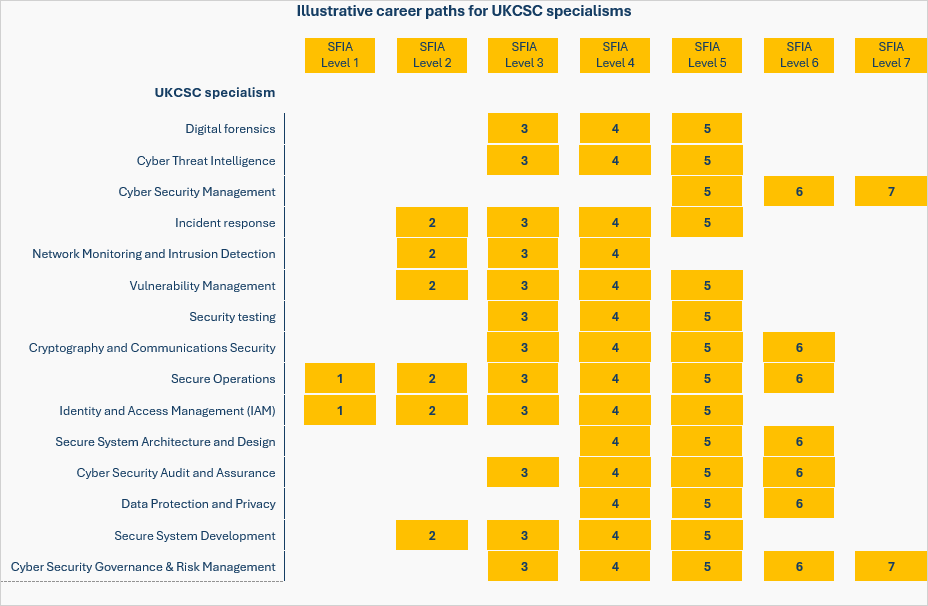
We can apply the SFIA levels to the UK Cyber Security council (UKCSC) specialisms. The actual roles and levels will be dependent on the employer and the nature of their business and operating model.
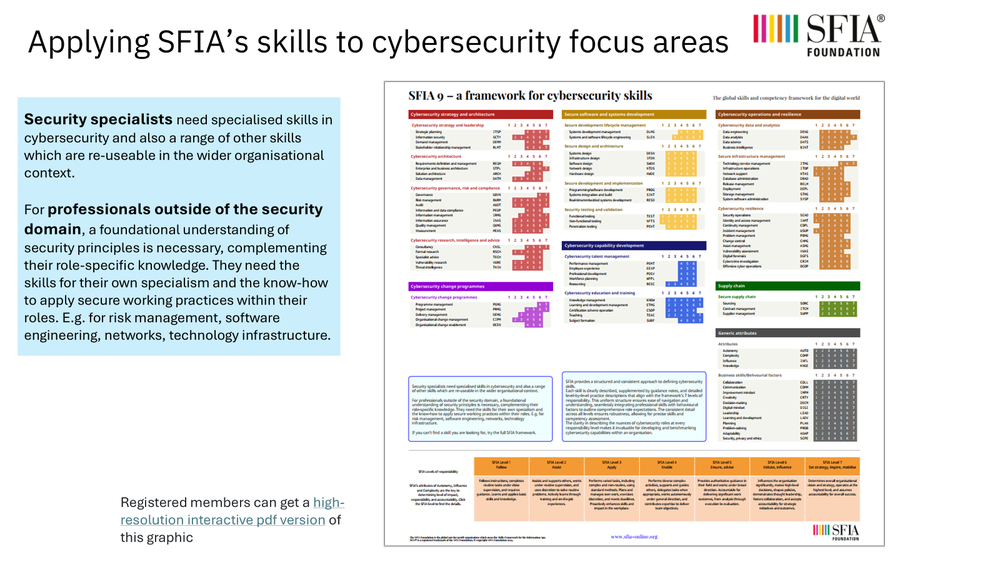
Because SFIA is a broad-based framework it includes skills for specialist cyber security roles but also adjacent roles and specialisms who apply secure working practices within their roles.
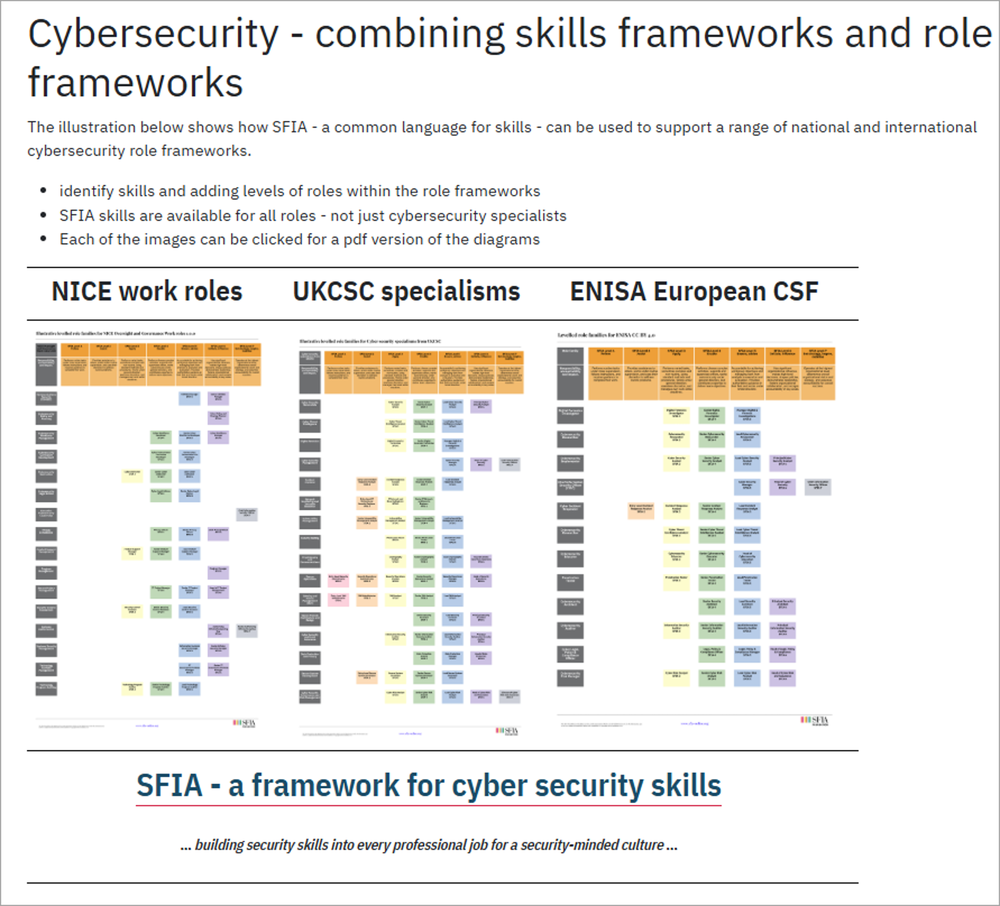
SFIA is a neutral and agnostics skills framework. It can be applied to a wide range of role frameworks. We have mappings of SFIA skills to the roles defined in all the major cybersecurity frameworks including UKCSC, NICE and ENISA.
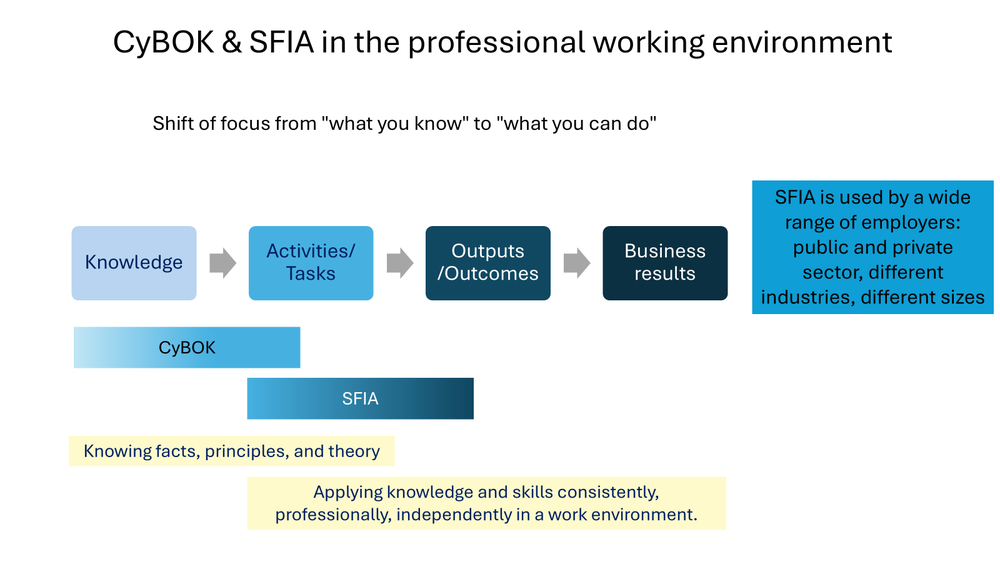
CyBOK and SFIA are complementary.
Mapping SFIA skills and CyBOK Knowledge Areas to UKCSC Specialisms
The mappings bring together
- Specialisms from UKCSC,
- Skills, levels of responsibility and behavioural factors from SFIA and
- Knowledge areas (KAs) from CyBOK
The mappings of CyBOK KAs to UKCSC specialisms is from the Cyber Career Framework published on the UKCSCS web site.
Notes on the mapping of SFIA skills to the UKCSC Specialisms
- The SFIA skill names in the skills tables for each specialism link directly to the full skill descriptions on the SFIA website. The numbers show the range of responsibility levels in the SFIA framework.
- This list highlights the most relevant SFIA skills for the role. These do not prescribe or recommend an organisation or team design.
- To use the SFIA skills to define cybersecurity roles and jobs, employers should take some time to learn about SFIA and clarify what you are trying to achieve and the outcomes you want from skills profiles. You can then tailor for your own use.
- Your organisation’s priorities and context will determine which skills and levels are required.
- For example, larger organisations may use specialised jobs/roles, while smaller organisations may combine several roles into one job.
- Review the SFIA levels to select relevant competency levels for your jobs/roles.
- Use SFIA levels to create graduated career steps of increasing responsibility and impact. Apply your own role/job titles and prefixes for seniority.
- If you cannot find what you need, try SFIA views, the full framework, or the A–Z list.
- try to limit SFIA skills per role. Five to seven skills provide focus; many roles need fewer.
- The framework also defines workplace skills/behavioural factors which complement technical skills. Success in cybersecurity roles depends not only on expertise but also on navigating business environments and motivating others.
- SFIA behavioural factors include collaboration, communication, creativity, decision-making, digital mindset, leadership, learning and development, planning, problem-solving, adaptability, improvement mindset, and security, privacy and ethics.
- The specific workplace factors and levels required will depend on organisational priorities and context.
The mappings for each of the UKCSC specialisms
Purpose: Design, develop, test, implement and operate of a system or product to provide cryptographic and/or secure communications.
Example responsibilities:
As a Cryptographer, you may:
- design security protocols, including key management rules
- assess the threats posed by changes in technology
- investigate how emerging technologies can be used to increase both agility and security
- produce analyses, reports and presentations
- supervise the manufacture and management of cryptographic keys
- develop new cryptographic primitives, such as algorithms (this is a very rare requirement)
In Communications Security, you may:
- advise systems developers or implementers on suitable communications security components
- build or support the integration of communications security elements in new systems
- support public key infrastructure (PKI) systems, including by managing digital certificates
- create and maintain meticulous records of PKI certificate details, especially when they expire
- operate and maintain secure communications systems
- ensure that the processing of individual messages adheres to the handling requirements of classification levels (particularly in government and military roles)
- manage alternative communication channels for special classes of messages
- assure the effectiveness of communications security systems, including through regular and rigorous audits
- oversee the strategic alignment and delivery of cluster-specific Cryptographic materials
- manage a cryptographic programme, including the proper control of commercial or Governmental key material
- support, supervise and manage more junior colleagues
Example job titles: Cryptography Analyst, Cryptography Systems Consultant, Cryptosecurity Engineer, Information Security Specialist, Network & Security Architect, Platform Solution Engineer, Research Engineer, Quantum Researcher, Secure Communications Engineer, Security Engineer, Security Consultant, Space/C4ISTAR Systems Engineer, Senior Security Engineer, Senior Security Research Engineer, Senior Principal Cryptosecurity Engineer, Senior Cryptography Security Analyst, Senior IT Assessor/Trainer, Head of Communications Security & Assurance
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||||||||||||||||
|
|
||||||||||||||||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||||||||||||||||
Purpose: Verify that systems and processes meet the specified security requirements and that processes to verify on-going compliance are in place.
Example responsibilities:
- assess the correctness of cyber security risk assessments and risk management plans, taking account of the organisation’s business goals
- produce detailed plans for cyber security audits
- use specific auditing tools to conduct efficient audits
- audit the implementation, operation and maintenance of security controls
- review compliance with legal and regulatory requirements
- provide expert advice on audit, assurance and risk management
- implement the Cyber Security Policy, Standards and Cyber Security Assurance Framework
- write formal reports, and sometimes deliver oral briefings, on the findings of audits and compliance reviews
- present findings to colleagues and managers, in both cyber security and general roles
- convince stakeholders of the importance of audit, assurance and security
Example job titles: Technology Risk Assurance Trainee, Cyber Assurance Manager, Security Assurance Coordinator, Business Assurance Manager, Information Cyber Security & Assurance Manager, Technology Resilience Assurance Specialist, Insurance Security Supplier Assurance Analyst, Supplier Security Assurance Manager, Information Security Consultant, Information Security Auditor, Cyber Security Audit and Compliance Lead, Head of Security, Governance Risk & Compliance, Head of Cyber Security and Information Assurance
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||
|
|
||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||
Purpose: Protect the security of an organisation’s information systems and data by setting policies, monitoring compliance and following defined procedures to identify, assess and manage risks from external and internal threats.
Example responsibilities:
- draft cyber security policies and procedures, taking account of an organisation’s legal, regulatory and operational requirements
- monitor compliance with policies
- identify cyber security risks, posed by the combination of vulnerabilities and threats, to the security of an organisation’s information systems and data
- assess the impact and likelihood of identified cyber security risks
- depending on the level of responsibility and the severity of specific risks, propose measures - including avoidance, mitigation, sharing and acceptance - to manage risks
- create and maintain a risk register or include the cyber security risks in the organisation’s overall risk register
- identify the requirement for policies and procedures and monitor their production and updating
- approve policies and procedures
- oversee the monitoring of compliance with agreed policies and procedures and report on this to senior management
- set up and maintain the arrangements for managing cyber security risk, including agreeing organisational structures and formalising lines of authority
- engage with heads of business departments to demonstrate the cyber risks which the organisation faces through existing processes and to recommend changes to them
- assess and report on the effectiveness of risk management standards and policies
- contribute to an organisation’s high-level risk strategy and the definition of its risk appetite
- manage governance and risk management professionals
Example job titles: Technology Risk & Controls Analyst, Cyber Risk & Compliance Manager, Cyber Risk Analyst, Cyber Risk Consultant, GRC Risk Management Senior Associate, Information Security Risk Analyst, IT Risk and Compliance Manager, IT Security and Risk Manager, Information Security Consultant, Information Security Manager, GRC Officer, Technology Risk Oversight Officer
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||||||||
|
|
||||||||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||||||||
Purpose: Ensure that the cyber security efforts and resources of the organisation are applied efficiently and effectively to protect both its systems and services and the information it holds.
Example responsibilities:
- ensure that the organisation’s cyber security policies and controls remain appropriate and proportionate to the assessed risks, and are responsive and adaptable to the changing threat environment, business requirements and relevant laws and regulations
- ensure that the organisation’s cyber security practice supports the business rather than restricts it
- in consultation with other managers, develop and implement a cyber security strategy
- manage the staff and resources of a cyber security team or the department to deliver the necessary cyber security controls and responses as efficiently as possible
- ensure that the cyber security team or department meets the organisation’s standards on equality and inclusion and supports the values and ethical aims of the organisation
- drive the professional development of the team or department’s cyber security staff
In addition, the Chief Information Security Officer (CISO) (or whichever role is responsible for overall cyber security functions):
- as part of the senior management team, contributes to the organisation’s strategy, pursuit of high standards of behaviour and efficiency
- is the primary point of contact on Cyber Security issues with key stakeholders across the organisation and outside
- represents the interests of the cyber security team or department and its staff in decision-making at higher levels, including at enterprise level
- advises and informs the organisation’s senior managers on the effectiveness of the cyber security strategy
Example job titles: Head of Cyber Security, Cyber Security Manager, Chief Information Security Officer (CISO), Director of Information & Cyber Security.
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||||||||||||
|
|
||||||||||||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||||||||||||
Purpose: Research and report on the cyber threats to organisations’ security, to enable the organisation to focus its resources on addressing the risks it faces.
Example responsibilities:
- support and lead the delivery of cyber security assessments and action recommendations to stakeholders at technical, managerial and executive level
- act as part of the Incident Response team where appropriate and provide operational cyber intelligence support during ongoing incidents
- research threats, Indicators of Compromise (IoCs) and threat actor Tactics, Techniques and Procedures (TTPs) to support Threat Hunting, Signature Development and Threat Intelligence Platform (TIP) processes
- evaluate and refine available technical intelligence feeds to drive maximum value
- work closely with the vulnerability management team to keep them updated on the latest threats
- maintain detailed threat actor profiles on adversaries of interest, covering their tactics, techniques and procedures, motivations, goals and strategic objectives
- establish mutual technical intelligence sharing with credible external sources
- identify research gaps and opportunities
Example job titles: Cyber Threat Intelligence Analyst, Intelligence Analyst, Threat Analyst, Cyber Risk Modeler, Cyber Threat Intelligence Specialist, Senior/Lead Cyber Threat Intelligence (Manager), Director of Security Operations
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||
|
|
||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||
Purpose: Ensure that the most important assets of an organisation are protected from theft or exposure to the wrong people, and that the organisation avoids the consequences of breaching data protection laws and regulations.
Example responsibilities:
- provide support in designing and documenting the data privacy requirements
- support the Head of Data Protection and Privacy in drafting and maintaining data privacy controls and measures
- assist the Head of Data Protection and Privacy in handling data or privacy breaches in accordance with policies and procedures
- submit data breach notifications to the Information Commissioner's Office (ICO) under Privacy and Electronic Communications Regulations (PECR) and the Data Protection Act
- support the creation and maintenance of mapping for all data flows
- undertake information security and data and privacy risk compliance audits to provide recommendations on improving protection
With more experience, you might also:
- provide subject matter expertise input and guidance to help colleagues and suppliers achieve desired data protection controls
- take a leading role in the organisation's incident response provision
- promote and facilitate awareness of data protection requirements and the related risk across the organisation through generic and targeted training
Example job titles: Information Security Analyst, Information Security Manager, Data Protection/Privacy Analyst, Data Protection Manager, Data Protection Consultant, Senior Data Protection/Privacy Consultant, Senior Data Protection Risk & Compliance Manager, Senior/Lead) Data Protection/Privacy Officer, Senior InfoSec Architect Data, Senior Consultant - Data/Privacy.
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||
|
|
||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||
Purpose: Use detailed technical knowledge and sophisticated tools and techniques to acquire, analyse and report on the data contents of devices and systems, whether as part of a response to a security incident or an investigation into possible criminal behaviour.
Example responsibilities:
- triage a set of devices, systems and software components to identify priorities for investigation
- physically disassemble and examine computers and related hardware
- use specialist tools and techniques to retrieve data from devices and systems, either directly or remotely, including by imaging storage media
- analyse files, data elements and memory contents to find evidence of malicious or illegal activity
- analyse malicious software to understand attack techniques, identify vulnerabilities and attribute the activity to those responsible
- handle materials and data to avoid contamination or corruption, possibly in line with chain of custody rules
- log every significant action
- produce formal reports on the investigation, often to the standard of evidential submission
Example job titles: Digital Forensic Investigator, Digital Forensics & Incident Response Specialist, Digital Forensics and Data Management Analyst, Digital Device Data Recovery Practitioner, Digital Forensic Technician, Senior Digital Forensics and Incident Response Specialist, Police Digital Investigator, Senior Digital Forensic Investigator, Digital & Forensic Investigations Manager
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||
|
|
||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||
Purpose: Managing policies, procedures and controls to ensure that only authorised individuals access information or computer-controlled resources.
Example responsibilities:
- perform routine administration tasks associated with accessing the Trusted ICT Network and Systems, including:
- managing users’ access credentials; and withdrawing and maintaining access in line with authorised service requests
- fulfil service requests for starters, movers and leavers in relation to user account management, by:
- updating user information; creating and modifying email distribution lists; and creating or modifying security groups
- design, develop, deploy and maintain identity and access management services and applications, including:
- local and federated authentication and authorisation systems: their backend directories; and databases
- identify opportunities for improving the IAM strategy, policies and processes
- investigate records of user actions and system processes when a security incident is suspected to have occurred
- assess and manage risks to the effectiveness and security of the IAM system
Example job titles: Identity & Access Management - Support Assistant, Identity & Access Management Analyst, Identity & Access Management Engineer, Identity & Access Management Specialist / Consultant / Director, Digital Identity Security Consultant, Cyber Manager - Identity & Access Management
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||||||||||||
|
|
||||||||||||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||||||||||||
Purpose: Protect the security of an organisation’s information systems and data, by following defined procedures to analyse and respond to cyber security breaches. Incident Response may also first detect the breaches and design and implement measures to prevent a recurrence.
Example responsibilities:
- respond to alerts from monitoring/detection systems within defined SLAs
- use configured tools and scripts to identify potential cyber security breaches
- following detailed procedures, analyse, respond to and/or escalate cyber security incidents
- analyse the source, nature and impact of breaches to support threat intelligence
- monitor security appliance health, performing basic troubleshooting of security devices and escalating severe problems to engineers
- contribute to the development of incident response capabilities, policies and procedures
- maintain logs of all actions taken
Example job titles: Cyber Incident Response Analyst, Cyber Incident Responder, Cyber Security Incident Response Analyst, Incident Response Specialist, Threat Intelligence Response Analyst, SOC Analyst, Cyber Intelligence Analyst
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||
|
|
||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||
Purpose: Monitor network and system activity to identify unauthorised actions by users or potential intrusion by an attacker.
Example responsibilities:
- configure, monitor, manage and troubleshoot network defence tools
- audit systems, identify problematic areas and implement strategic solutions
- monitor security alert queues, investigate and triage events based on criticality and take actions to mitigate threats
- manage and act as an escalation point for Network Security technical issues
- create or maintain network security policies
- manage key relationships with security partners and other internal departments
- manage relationships with external parties such as security vendors
Example job titles: Network (Support/Security) Manager, Network Security Architect (although this can also be applied to pure network design roles), Security Monitoring Analyst, Cyber Security Analyst, Monitoring Analyst, IT Security Analyst, Network Operations Engineer, IT Network and Security Engineer, Senior Intrusion Analyst, Senior Security Network Engineer
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||||||||
|
|
||||||||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||||||||
Purpose: Managing an organisation’s information systems, networks and processes according to security standards and requirements, to protect against attacks and accidental security incidents.
Example responsibilities:
- manage identification, authentication and authorisation controls, including directories
- monitor system performance, including security incident metrics
- ensure that system processes, such as backups, are effective and in compliance with agreed protocols
- manage discrete development and test environments
- manage the transition to operation of new components and systems to minimise the risk to the security of other systems and current services
- ensure that updates (patches) to externally supplied software and hardware are applied quickly but safely
- support users in viewing and processing data according to agreed access controls
- manage the recovery of services after a security incident has been resolved
With more experience, you may also:
- be responsible for the overall performance and security of live systems
- plan the work of other colleagues
- set and monitor compliance with operational standards, particularly ones concerned with security
- select and implement performance and security monitoring tools
- monitor the effectiveness of the operations and identify changes which will improve performance
- work with managers in other teams to ensure effective cyber security across the organisation
- recruit, train and assess others
Example job titles: Cyber Security Engineer, Cyber Engineer, Cyber Security Analyst (although this also covers wide-ranging, generalist cyber security roles), Infrastructure Support Engineer, System Operations Engineer - Cyber Specialist, Security Operations - Technical Specialist, IS Operations & Security Manager.
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||||||||
|
|
||||||||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||||||||
Purpose: Decide on the essential security structure of the information systems which an organisation develops and runs and verifies that the delivered systems conform to the design.
Example responsibilities:
- agree high-level business requirements with non-technical colleagues
- plan, research and design secure software development and delivery systems, with objectives like security, speed, scalability and robustness at the core
- create technical requirements and specifications for major software systems and subsystems
- estimate costings related to new designs
- ensure that systems are developed and implemented securely, according to the agreed design and relevant industry standards
- report on and present recommended solutions to technical and non-technical stakeholders
- review installations of new network devices
- provide expert software security advice (on design, coding, testing, etc.) to software developers, system operators and other colleagues
- research, including by consultation with specialist colleagues, potential cyber security threats
- stay up to date with emerging cyber security principles, standards and technologies
- oversee testing of final designs
- develop roadmaps of future cyber security technology developments and the implications for the organisation’s systems
- assist with capability, capacity, and operational planning activities
Example job titles: Security Architect, Secure Systems Architect, Application Security Architect, Software Cloud Architect, Software Applications Security Architect | Cloud, Software Security Architect, Cybersecurity Technical Architect, Chief Cloud Security Architect, Chief Security Architect, Senior Security Architect, Lead Cloud Security Architect
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||||||||||||||
|
|
||||||||||||||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||||||||||||||
Purpose: Development and updating of a system or product, in conformance with agreed security requirements and standards, throughout its lifecycle.
Example responsibilities:
- interpret requirements to hardware or software products that meet them
- develop the products using components, tools, techniques and methodologies which minimise the chance of creating vulnerabilities in the products
- integrate their products into more complex systems, including cloud-based systems
- design, execute and report on tests of the products
- identify, investigate and solve errors in the products
- use sophisticated platforms, including cloud-based platforms, to carry out the development and testing
- produce documentation on the products to guide implementers, system operators and administrators and, sometimes, end users
- respond to change requests by updating the products, in some environments, very frequently
With more experience, you may also:
- be responsible for the overall delivery of products to the implementation team or customers
- ensure that the development environment and the related processes are secure against the leaking of sensitive data or code or breaches which might allow to malefactors to manipulate products to create vulnerabilities
- plan the work of colleagues
- set and monitor compliance with development standards, particularly ones concerned with security
- select and implement methods and tools
- monitor the effectiveness of the development process and identify changes which will improve performance
- recruit, train and assess others.
Example job titles: Secure Development Lifecycle Specialist, Software Engineer, Software Development Engineer, Application Security Engineer, DevSecOps Engineer, Hardware Engineer, Electronics Design Engineer, Platform Engineer, Engineering Manager - Secure Cloud, Senior Security Engineer, DevSecOps Lead, Senior Software Engineer – Cybersecurity
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||||||||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||||||||||||||||||||||
|
|
||||||||||||||||||||||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||||||||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||||||||||||||||||||||
Purpose: Test a network, system, product or design, against the specified security requirements and/or for vulnerabilities (penetration testing).
Example responsibilities:
- test software and hosted platforms, to identify vulnerabilities
- carry out penetration testing of web applications, mobile applications, and internal infrastructure
- analyse code to assess its level of security and to find specific vulnerabilities
- manage the security testing process
- participate in complex simulated attacks on networks or systems
- work with other specialists, such as Cyber Threat Intelligence analysts, to keep updated with the latest threats/vulnerabilities
- produce written technical reports to a professional standard, for clients
- research potential vulnerabilities
- research potential new security mechanisms or methods, and develop promising options
- formally brief clients and colleagues
Example job titles: Cyber Security Consultant, Cyber Penetration Test Specialist, Ethical Hacker, Information Security Specialist, Penetration Tester, Penetration Test Consultant, Security Consultant.
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||||||
|
|
||||||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||||||
Purpose: Protect information systems and assets by identifying and closing off vulnerabilities in devices, systems and networks.
Example responsibilities:
- stay up to date with reports of vulnerabilities in ff-the-shelf software and hardware
- research potential vulnerabilities in the organisation’s systems
- identify and prioritise vulnerabilities
- propose and implement mitigations for identified vulnerabilities
- work on different projects such as patch compliance and sector-specific compliance (for example, with PCI-DSS standards)
- work with our internal and external Certifying Authorities (CA)
- configure ADFS and remote access solutions
- run network and application vulnerability scans
- provide support to and work directly with clients on vulnerabilities
- write and deliver client reports
Example job titles: Cyber Security - Vulnerability Manager, Vulnerability Management Analyst, Vulnerability Scanning Specialist, Infrastructure Engineer SCCM/Vulnerability Remediation, Infrastructure Analyst - Vulnerability Management, IT Specialist Info Security, Senior/Lead Threat and Vulnerability Analyst, Senior/Lead IT Security Analyst - Vulnerability Management
SFIA skills– each skill name is hyperlink to the full skill definition for all the SFIA levels indicated |
|||||||||||||||||
|
Look at these SFIA skills first |
Other SFIA skills to consider |
||||||||||||||||
|
|
||||||||||||||||
CyBOK Knowledge areas– see the CyBOK knowledgebase for details of each KA. Mapping of KAs to specialisms is from UKCSC Career Framework. |
|||||||||||||||||
|
Core knowledge
|
Related knowledge
|
Wider knowledge
|
|||||||||||||||