CyBOK SFIA mapping
This page maps the Cyber Security Body of Knowledge (CyBOK) knowledge areas to the Skills Framework for the Information Age (SFIA)
References to CyBOK © Crown Copyright, The National Cyber Security Centre 2021, licensed under the Open Government Licence: http://www.nationalarchives.gov.uk/doc/opengovernment-licence/.
The Cyber Security Body Of Knowledge (CyBOK) is a comprehensive Body of Knowledge to inform and underpin education and professional training for the cyber security sector.
- The CyBOK project aims to bring cyber security into line with the more established sciences by distilling knowledge from major internationally-recognised experts to form a Cyber Security Body of Knowledge that will provide much-needed foundations for this emerging topic.
On this page:
- Background to the SFIA-CyBOK Mapping
- Introduction to SFIA for CyBOK Users
- SFIA Levels of Responsibility
- Progression in SFIA levels is about responsibility accountability and impact
- Knowledge types and SFIA level application
- Diagrams and illustrations
- Illustration of career levels in the cyber security specialisms
- Illustrative career paths for the UKCSC specialisms
- Applying SFIA skills to cyber security focus areas
- Combining skills frameworks and role frameworks for cyber security - NICE work roles, UKCSC Specialisms, ENISA
- CyBOK and SFIA in professional working environment
- Mapping CYBOK and SFIA
- The mapping of the 21 CyBOK Knowledge Areas to SFIA skills
Background to the SFIA-CyBOK Mapping
Introduction
This document maps the Cyber Security Body of Knowledge (CyBOK) knowledge areas to the Skills Framework for the Information Age (SFIA) to help both academic and industry audiences connect theoretical/foundational cyber security knowledge with professional competencies in practice.
For industry professionals using SFIA
- SFIA provides structured professional competencies across seven levels of responsibility, from following procedures to setting enterprise strategy.
- This mapping shows how the knowledge areas outlined in CyBOK can deepen understanding of why certain practices work, enabling more effective application of SFIA skills, particularly at responsibility levels where judgment and adaptation are crucial.
For academics and educators familiar with CyBOK
- CyBOK organises cyber security knowledge into structured knowledge areas designed primarily to codify “the foundational knowledge in cyber security for education and professional training”.
- This mapping demonstrates how that conceptual knowledge supports measurable professional competencies in industry roles, showing the practical application of theoretical concepts across different levels of organisational responsibility.
The integration value
- Combining CyBOK's theoretical depth with SFIA's structured competency framework helps develop professionals who can both execute effectively and make sound strategic judgments
- The theoretical understanding enables better adaptation of standard practices and communication of why certain practices are needed
Introduction to SFIA for CyBOK Users
SFIA Foundation and the SFIA community
- Global adoption – SFIA is used in 200+ countries, with cyber security applications in the UK, US, Canada, Australia, NZ and beyond.
- Trusted governance – stewarded by the not-for-profit SFIA Foundation, with updates driven by a design authority and international consultation.
- Diverse contributors – community includes governments, universities, professional bodies, employers, and practitioners.
- Open and accessible – free for individuals and most employers, with translations into 11 languages and supporting resources.
- Practical support – guidance notes, example role profiles, mappings to standards and other frameworks
Understanding SFIA Skill Structure
Before examining the mapping, it's important to understand how SFIA skills are defined. Unlike simple skill lists, each SFIA skill provides:
- Detailed guidance explaining the scope of activities and typical responsibilities
- Level descriptions showing progression from basic assistance to strategic leadership
- Collaboration context identifying which other skills typically work together
- Business integration showing how technical skills connect to organisational outcomes
This structure means SFIA skills describe comprehensive professional competencies that integrate technical knowledge, business understanding, and leadership capabilities.
Structure and content of the SFIA Framework
- Seven levels of responsibility – a progression from following instructions (Level 1) to setting strategy (Level 7).
- Over 140 professional skills – covering not only cybersecurity but also business, data, digital, and organisational skills that cyber roles depend on.
- Includes definitions and of business skills/behavioural factors such as communication, decision-making, collaboration, leadership, problem-solving
- Task/activity/competency orientation – skills are described as tasks and outcomes at each level, not just as knowledge statements.
- Reusability across contexts – the same SFIA skill can apply in cyber, software, data, or business settings, making cross-domain mobility clear. This supports secure-by-design responsibilities.
- Integration with knowledge; CyBOK = knowledge, SFIA = competency; they reinforce each other rather than duplicate. The mapping of SFIA skills and CyBOK knowledge areas to the UK Cyber Security Council’s specialisms provides an illustration of this.
SFIA Levels of responsibility
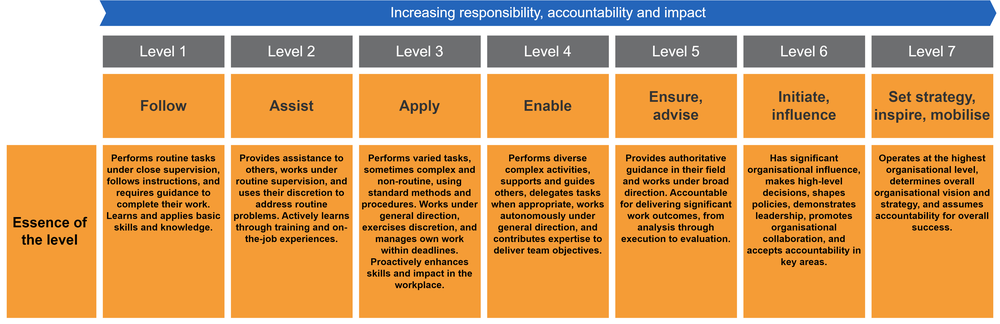
SFIA provides a structured approach to defining and developing professional skills and competencies. At its core, SFIA uses a seven-level structure to describe both professional skills and generic attributes, creating a consistent framework for assessing and developing capabilities. Full details at How SFIA works - Levels of responsibility and skills.
The seven levels of responsibility range from Level 1 (the lowest) to Level 7 (the highest). Each level represents increasing expertise and responsibility in professional roles.
Each level is carefully defined to be:
- Progressive (Building on the previous level's requirements),
- Distinct (Clearly differentiated from adjacent levels), and
- Consistent (Using uniform criteria across all skills).
The levels are characterised by specific behaviours, values, knowledge and characteristics that indicate an individual's operational capability at that level. The concise essence statements provide a distilled view of the unique characteristics of each level. They help users easily distinguish between levels and understand progression without needing to dive into detailed descriptions.
Generic attributes
SFIA defines how professionals operate at each level through:
- Autonomy: Level of independence and accountability
- Influence: Reach and impact of decisions and actions
- Complexity: Range and intricacy of responsibilities
- Business Skills: e.g. Communication, planning, problem-solving, collaboration
- Knowledge: Depth and breadth of understanding required
Progression in SFIA levels is about responsibility accountability and impact
We can illustrate this by looking at one of the SFIA skills:
- The full skill description is here Information security (SCTY)
- The short description of this SFIA skill is "Defining and operating a framework of security controls and security management strategies"
- The table below summarises the responsibility and impact at each level of the Information security skill - from SFIA level 2 to level 7.
- Note how the progression moves from implementing existing controls to setting enterprise strategy. A Level 7 professional doesn't necessarily know more technical details about specific security techniques than a Level 4 specialist - they apply broader judgment about organisational risk and strategy.
|
SFIA level |
Focus of responsibility |
Typical impact |
|
2 – Assist |
Supports the implementation and monitoring of defined security controls under supervision. |
Contributes to consistent, reliable execution of established security procedures. |
|
3 – Apply |
Applies and maintains specific controls, identifying and escalating security risks when needed. |
Maintains safe and effective security operations through competent, independent application of controls. |
|
4 – Enable |
Guides others in applying controls and conducts security risk and impact analysis. |
Strengthens team performance and assurance through expert advice and proactive risk management. |
|
5 – Ensure, advise |
Leads the development and application of security strategies, policies, and architectures to manage identified risks. |
Delivers organisation-wide security outcomes by combining strategic guidance with active oversight of complex operations. |
|
6 – Initiate, influence |
Shapes corporate security policy and aligns it with business strategy. |
Integrates security into strategic planning, driving organisational alignment and capability. |
|
7 – Set strategy, inspire, mobilise |
Directs enterprise information security strategy and governance. |
Builds organisational resilience through strategic leadership and alignment of security with business vision. |
Seven Levels of Responsibility
SFIA levels represent increasing organisational responsibility and strategic impact:
- Levels 1-3: Follow, Assist, Apply - executing established procedures and practices
- Levels 4-5: Enable, Ensure and Advise - guiding others and ensuring effectiveness
- Levels 6-7: Initiate and Influence, Set Strategy - organisational leadership and strategic direction
Critical understanding: Higher SFIA levels are about broader organisational responsibility and impact, not deeper technical expertise. E.g. A Level 7 professional sets enterprise strategy and mobilises resources; they don't need to know more technical details than a Level 4 specialist.
Understanding CyBOK structure for SFIA users
CyBOK is primarily intended as a guideline for curriculum developers, not as a direct learning resource for practitioners. Key structural elements include:
Knowledge areas vs. Professional skills
- CyBOK organises theoretical knowledge into domains such as "Risk Management & Governance" or "Software Security." These describe what needs to be understood conceptually, not how that understanding is applied in professional roles.
- SFIA skills such as "Information Security (SCTY)" describe professional competencies that draw upon multiple CyBOK knowledge areas.
Academic vs. Industry focus
- CyBOK emphasises theoretical foundations, research findings, and conceptual frameworks.
- SFIA emphasises professional application, business integration, and organisational impact. The mapping shows how theoretical depth supports practical competency.
Curriculum design tool
- CyBOK helps educators design comprehensive cyber security curricula.
- Although some industry professionals may reference specific knowledge areas for deep understanding, it is professional education and certification programs that are most influenced by CyBOK's knowledge organization.
Knowledge types and SFIA level application
→ more details in this "Briefing' for Employers"
Most cybersecurity roles require a mix of knowledge types:
- Procedural knowledge: knowing how to follow steps, use tools, and perform defined tasks.
- Declarative or conceptual knowledge: knowing about systems, frameworks, and principles — the “why” that sits behind procedures.
- Conditional knowledge: knowing when and why to act, making decisions, using judgment in context.
The relationship between CyBOK knowledge domains and SFIA competencies varies by responsibility level:
Procedural knowledge
- What it involves: Following established procedures, implementing standard practices, applying known solutions and tools
- Knowledge sources: Organisational procedures, vendor tool training, entry-level certifications, on-the-job learning
- CyBOK relevance: The content of the CyBOK knowledge areas should not be expected to cover procedural knowledge. The scope of each CyBOK Knowledge area can help in identifying what conceptual understanding may be useful to provide context to procedures and practices, but detailed theoretical knowledge is often not required.
- Example: Following incident response playbooks, implementing configured security controls, using SIEM tools
Conceptual knowledge
- What it involves: Understanding principles, adapting practices to context, explaining why approaches work
- Knowledge sources: Professional certifications, university education, industry frameworks - often influenced by CyBOK knowledge areas
- CyBOK relevance: Knowledge domains provide theoretical foundations that enable effective adaptation and guidance
- Example: Customising risk frameworks for organisational context, designing security architectures for specific requirements
Judgment/Decision-making knowledge
- What it involves: Strategic decisions, knowing when standard approaches don't apply, organisational adaptation
- Knowledge sources: Professional experience, mentoring, executive education, cross-industry exposure
- CyBOK Relevance: Theoretical frameworks help recognise when and why adaptations are needed, but judgment primarily comes from experiential learning
- Example: Setting enterprise security strategy, making risk appetite decisions, designing governance structures
How knowledge sources support SFIA skills
The knowledge required for effective performance of SFIA skills can come from multiple sources:
Formal Education and Professional Development
- University degrees with curricula often influenced by CyBOK knowledge areas
- Industry certifications (CISSP, CISM, Security+) covering both theoretical and practical aspects
- Professional training on specific frameworks and standards
- CyBOK knowledge areas – used as a reference for identifying theoretical understanding needed
Industry standards and frameworks
- Technical standards (ISO 27001, NIST Cybersecurity Framework, industry-specific requirements, NICE cybersecurity work roles, UKCSC specialisms)
- Best practice frameworks (ITIL, TOGAF, COSO) for integration with broader organisational practices
- Regulatory requirements (GDPR, HIPAA, sector-specific compliance)
Organisational context
- Business knowledge (strategy, processes, financial constraints, stakeholder expectations)
- Technical environment (current infrastructure, planned changes, vendor relationships)
- Cultural factors (risk appetite, change readiness, communication preferences)
Professional experience
- Practical implementation experience with various technologies and approaches
- Cross-functional collaboration with legal, finance, operations, and other business areas
- Leadership and communication skills for influencing stakeholders and driving change
We can apply the SFIA levels to typical career levels found in the cyber security domain.
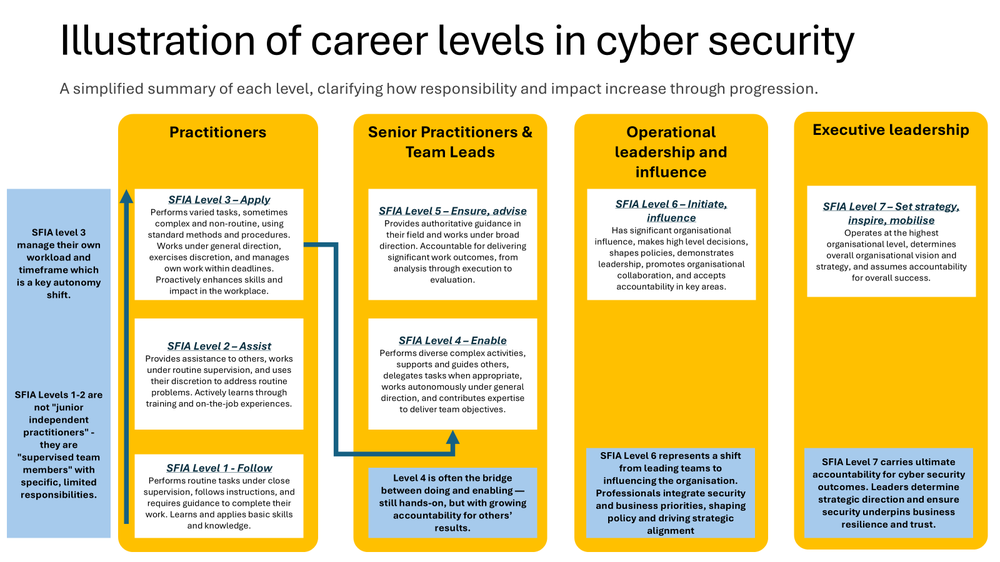
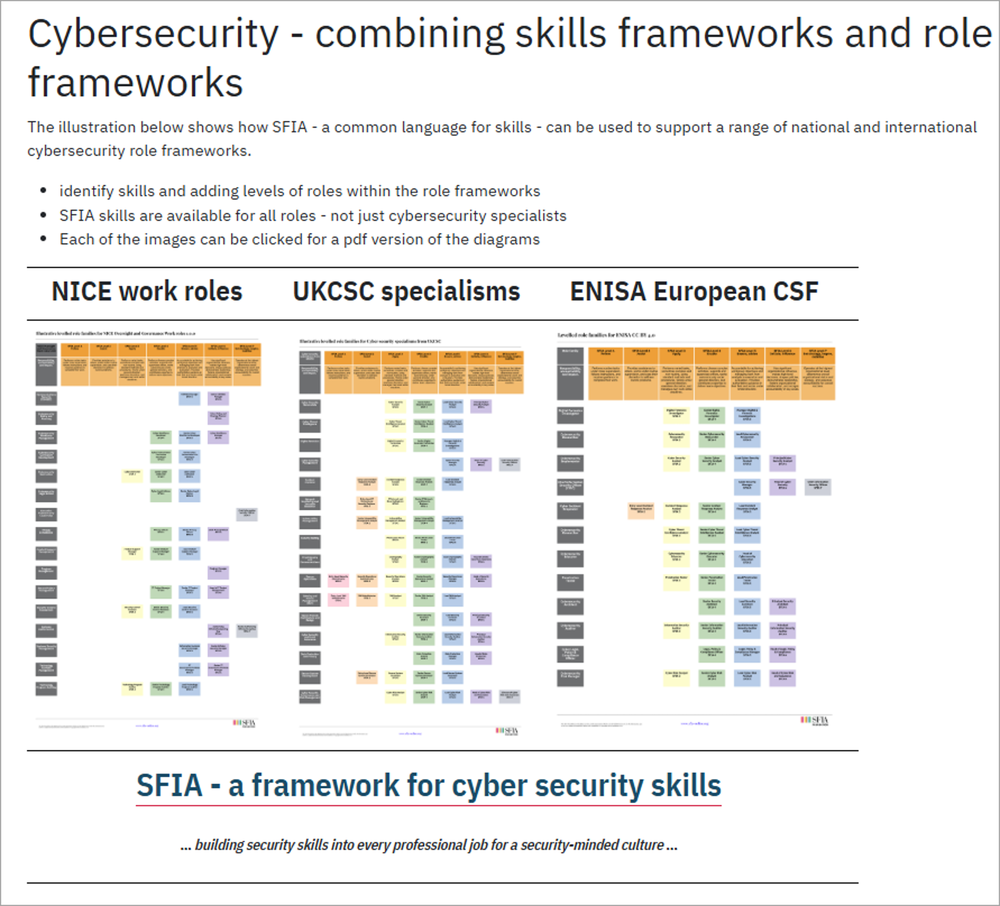
We can also apply the SFIA levels to typical industry roles - e.g. the diagram below shows SFIA levels mapped to the UK Cyber Security council (UKCSC) specialisms. The actual roles and levels will be dependent on the employer and the nature of their business and operating model.
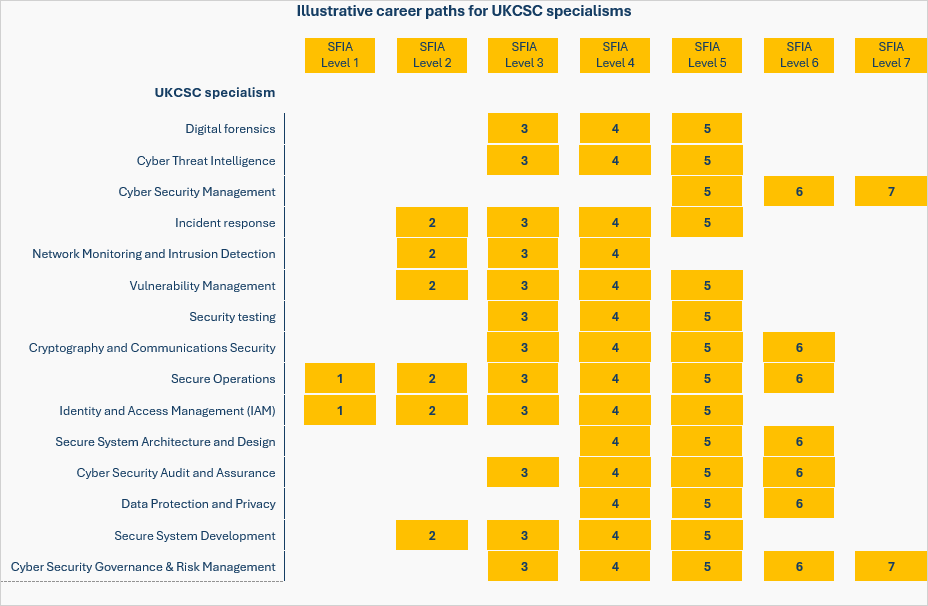
Because SFIA is a broad-based framework it includes skills for specialist cyber security roles but also adjacent roles and specialisms who apply secure working practices within their roles.
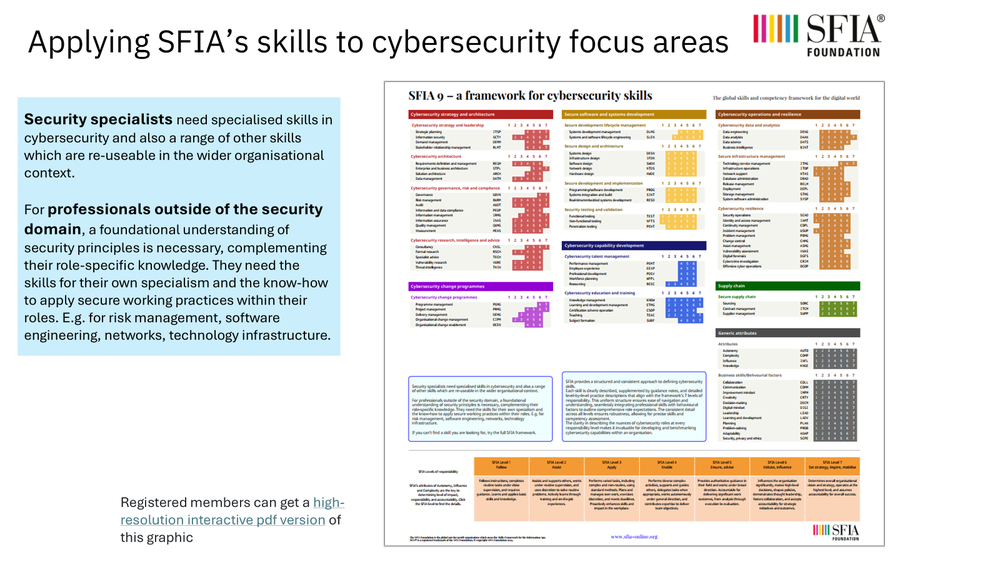
SFIA is a neutral and agnostics skills framework. It can be applied to a wide range of role frameworks. We have mappings of SFIA skills to the roles defined in all the major cybersecurity frameworks including UKCSC, NICE and ENISA.
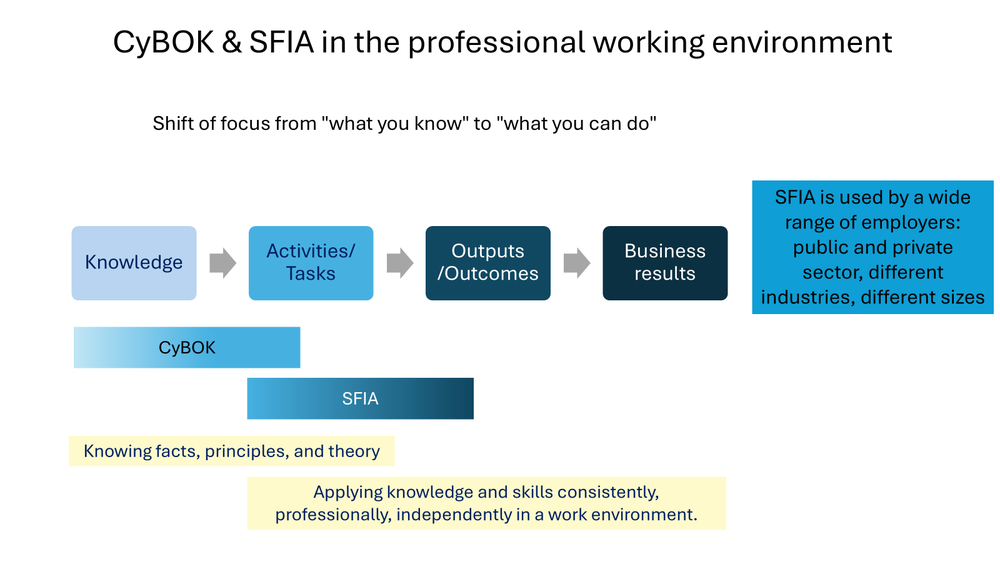
CyBOK and SFIA are complementary.
Mapping CyBOK Knowledge Areas to SFIA skills
Key Principles of the Mapping
CyBOK as theoretical foundation
CyBOK knowledge areas provide conceptual depth that enhances professional judgment but don't define professional competencies. The theoretical understanding helps professionals know when and why to adapt standard practices, communicate more effectively with other disciplines, and make sound decisions in novel situations.
SFIA as professional application
SFIA skills describe how theoretical knowledge manifests in professional roles, integrating technical understanding with business context, stakeholder management, and organisational leadership. Higher SFIA levels require broader judgment informed by theoretical principles but applied to organisational dynamics.
Multiple knowledge sources required
Effective professional performance requires integration of theoretical knowledge (which may be influenced by CyBOK KAs), industry standards, regulatory requirements, organisational context, and professional experience. Learning based on CyBOK KAs provides one important component but not a complete foundation.
Progression from procedure to decision-making and judgment
Lower SFIA levels primarily require procedural knowledge and standard practice application. Higher levels increasingly require conceptual understanding and judgment capabilities that benefit from theoretical depth, whether gained through formal education, professional development, or study of knowledge domains outlined in CyBOK.
Using this mapping
For professional development planning
- Identify which CyBOK knowledge areas provide theoretical foundation for your target SFIA skills
- Understand what additional business and interpersonal skills are needed beyond technical knowledge
- Recognise when and how theoretical depth supports progression to higher responsibility levels
For curriculum design
- See how academic knowledge areas translate to industry-relevant professional competencies
- Understand what business context and professional skills complement theoretical knowledge
- Design programs that prepare students for specific SFIA professional skills and responsibility levels
For organisational capability assessment
- Assess whether staff have sufficient theoretical foundation for their SFIA responsibility level
- Identify professional development needs that combine technical depth with business skills
- Understand collaboration patterns between different SFIA skills and knowledge domains
For career planning
- Understand how academic preparation relates to industry role requirements
- Identify knowledge gaps that may limit progression to higher responsibility levels
- Plan professional development that combines theoretical depth with practical business skills
The mapping of CyBOK Knowledge Areas to SFIA skills
- Risk Management & Governance
- Law & Regulation
- Human Factors
- Privacy & Online Rights
- Malware & Attack Technologies
- Adversarial Behaviours
- Security Operations & Incident Management
- Forensics
- Cryptography
- Operating Systems & Virtualisation Security
- Distributed Systems Security
- Formal Methods for Security
- Authentication, Authorisation & Accountability
- Software Security
- Web & Mobile Security
- Secure Software Lifecycle
- Applied Cryptography
- Network Security
- Hardware Security
- Cyber-Physical Systems Security
- Physical Layer & Telecommunications Security
Short description of this knowledge area
Security management systems and organisational security controls, including standards, best practices, and approaches to risk assessment and mitigation.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Defining and operating a framework of security controls and security management strategies. |
SCTY |
2 - 7 |
|
|
Defining and operating frameworks for decision-making, risk management, stakeholder relationships and compliance with organisational and regulatory obligations. |
GOVN |
6 - 7 |
|
|
Planning and implementing processes for managing risk across the enterprise, aligned with organisational strategy and governance frameworks. |
BURM |
2 - 7 |
|
|
Protecting against and managing risks related to the use, storage and transmission of data and information systems. |
INAS |
2 - 7 |
|
|
Delivering independent, risk-based assessments of the effectiveness of processes, the controls and the compliance environment of an organisation. |
AUDT |
2 - 7 |
|
|
Developing, implementing and testing a business continuity framework. |
COPL |
2 - 6 |
Short description of this knowledge area
International and national statutory and regulatory requirements, compliance obligations, and security ethics, including data protection and developing doctrines on cyber warfare.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Implementing and promoting compliance with information and data management legislation. |
PEDP |
4 - 6 |
|
|
Implementing and promoting ethical practices in the design, development, deployment and use of AI and data technologies. |
AIDE |
3 - 6 |
|
|
Defining and operating frameworks for decision-making, risk management, stakeholder relationships and compliance with organisational and regulatory obligations. |
GOVN |
6 - 7 |
|
|
Planning and implementing processes for managing risk across the enterprise, aligned with organisational strategy and governance frameworks. |
BURM |
2 - 7 |
Short description of this knowledge area
Usable security, social & behavioural factors impacting security, security culture and awareness as well as the impact of security controls on user behaviours.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Identifying users' behaviours, needs and motivations using observational research methods. |
URCH |
2 - 6 |
|
|
Understanding the context of use for systems, products and services and specifying user experience requirements and design goals. |
UNAN |
2 - 5 |
|
|
Producing design concepts and prototypes for user interactions and experiences of a product, system or service. |
HCEV |
2 - 6 |
|
|
Validating systems, products or services against user experience goals, metrics and targets. |
USEV |
2 - 6 |
|
|
Designing and developing resources to transfer knowledge, develop skills and change behaviours. |
TMCR |
2 - 5 |
|
|
Transferring knowledge, developing skills and changing behaviours using a range of techniques, resources and media. |
ETDL |
2 - 5 |
|
|
Planning, designing and implementing activities to transition the organisation and people to the required future state. |
CIPM |
2 - 6 |
|
|
Facilitates cultural and behavioural change by enabling individuals and teams to embed new ways of working and adapt to changes. |
OCEN |
4 - 6 |
|
|
Systematically analysing, managing and influencing stakeholder relationships to achieve mutually beneficial outcomes through structured engagement. |
RLMT |
4 - 7 |
Short description of this knowledge area
Techniques for protecting personal information, including communications, applications, and inferences from databases and data processing. It also includes other systems supporting online rights touching on censorship and circumvention, covertness, electronic elections, and privacy in payment and identity systems.
SFIA skills – click links for full skill description including levels
Comments
Looking at the Privacy & Online Rights Knowledge Area, this represents a different pattern from both Human Factors and Law & Regulation. This KA is much more technically specialised and targets a narrower audience.
“The goal of this knowledge area is to introduce system designers to the concepts and technologies that are used to engineer systems that inherently protect users’ privacy. We aim to provide designers with the ability to identify privacy problems, to describe them from a technical perspective, and to select adequate technologies to eliminate, or at least, mitigate these problems”.
From Privacy & Online Rights knowledge area, CyBOK
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Designing systems to meet specified requirements and agreed systems architectures. |
DESN |
2 - 6 |
|
|
Architecting and designing software to meet specified requirements, ensuring adherence to established standards and principles. |
SWDN |
2 - 6 |
|
|
Developing and implementing plans, policies and practices that control, protect and optimise the value and governance of data assets. |
DATM |
2 - 6 |
|
|
Protecting against and managing risks related to the use, storage and transmission of data and information systems. |
INAS |
2 - 7 |
|
|
Manages identity verification and access permissions within organisational systems and environments. |
IAMT |
1 - 6 |
Short description of this knowledge area
Technical details of exploits and distributed malicious systems, together with associated discovery and analysis approaches.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Manages and administers security measures, using tools and intelligence to protect assets, ensuring compliance and operational integrity. |
SCAD |
1 - 6 |
|
|
Testing the effectiveness of security controls by emulating the tools and techniques of likely attackers. |
PENT |
2 - 6 |
|
|
Developing and sharing actionable insights on current and potential security threats to the success or integrity of an organisation. |
THIN |
2 - 6 |
|
|
Conducting applied research to discover, evaluate and mitigate new or unknown security vulnerabilities and weaknesses. |
VURE |
2 - 6 |
|
|
Plans, executes and manages offensive cybersecurity operations, including target selection, electronic target folders and post-operation analysis. |
OCOP |
2 - 6 |
Short description of this knowledge area
The motivations, behaviours, & methods used by attackers, including malware supply chains, attack vectors, and money transfers.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Manages and administers security measures, using tools and intelligence to protect assets, ensuring compliance and operational integrity. |
SCAD |
1 - 6 |
|
|
Testing the effectiveness of security controls by emulating the tools and techniques of likely attackers. |
PENT |
2 - 6 |
|
|
Developing and sharing actionable insights on current and potential security threats to the success or integrity of an organisation. |
THIN |
2 - 6 |
|
|
Conducting applied research to discover, evaluate and mitigate new or unknown security vulnerabilities and weaknesses. |
VURE |
2 - 6 |
|
|
Plans, executes and manages offensive cybersecurity operations, including target selection, electronic target folders and post-operation analysis. |
OCOP |
2 - 6 |
Short description of this knowledge area
The configuration, operation and maintenance of secure systems including the detection of and response to security incidents and the collection and use of threat intelligence.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Manages and administers security measures, using tools and intelligence to protect assets, ensuring compliance and operational integrity. |
SCAD |
1 - 6 |
|
|
Developing and sharing actionable insights on current and potential security threats to the success or integrity of an organisation. |
THIN |
2 - 6 |
|
|
Identifying and classifying security vulnerabilities in networks, systems and applications and mitigating or eliminating their impact. |
VUAS |
2 - 5 |
|
|
Coordinating responses to a diverse range of incidents to minimise negative impacts and quickly restore services. |
USUP |
1 - 6 |
|
|
Managing the lifecycle of all problems that have occurred or could occur in delivering a service. |
PBMG |
2 - 5 |
|
|
Enabling data-driven decision making by extracting, analysing and communicating insights from structured and unstructured data. |
DAAN |
2 - 7 |
|
|
Developing systems that learn from data and experience, improving performance, accuracy and adaptability in dynamic environments. |
MLNG |
2 - 6 |
|
|
Developing, producing and delivering regular and one-off management information to provide insights and aid decision-making. |
BINT |
2 - 5 |
|
|
Designing, building, operationalising, securing and monitoring data pipelines, stores and real-time processing systems for scalable and reliable data management. |
DENG |
2 - 6 |
Short description of this knowledge area
The collection, analysis, & reporting of digital evidence in support of incidents or criminal events.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Recovering and investigating material found in digital devices. |
DGFS |
2 - 6 |
|
|
Investigates cybercrimes, collects evidence, determines incident impacts and collaborates with legal teams to protect digital assets. |
CRIM |
2 - 6 |
|
|
Coordinating responses to a diverse range of incidents to minimise negative impacts and quickly restore services. |
USUP |
1 - 6 |
|
|
Managing the lifecycle of all problems that have occurred or could occur in delivering a service. |
PBMG |
2 - 5 |
Short description of this knowledge area
Core primitives of cryptography as presently practised & emerging algorithms, techniques for analysis of these, and the protocols that use them.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Protecting against and managing risks related to the use, storage and transmission of data and information systems. |
INAS |
2 - 7 |
|
|
Conducting applied research to discover, evaluate and mitigate new or unknown security vulnerabilities and weaknesses. |
VURE |
2 - 6 |
|
|
Creating, analysing, implementing, testing and improving algorithms for numerically solving mathematical problems. |
NUAN |
4 - 7 |
Short description of this knowledge area
Operating systems protection mechanisms, implementing secure abstraction of hardware, and sharing of resources, including isolation in multiuser systems, secure virtualisation, and security in database systems.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Installing, managing and maintaining operating systems, data management, office automation and utility software across various infrastructure environments. |
SYSP |
2 - 5 |
|
|
Manages identity verification and access permissions within organisational systems and environments. |
IAMT |
1 - 6 |
|
|
Installing, configuring, monitoring, maintaining databases and data stores, ensuring performance and security and adapting to evolving technologies. |
DBAD |
2 - 5 |
|
|
Establishing and deploying an environment for developing, continually improving and securely operating software and systems products and services. |
SLEN |
3 - 7 |
|
|
Provisioning, configuring and optimising on-premises and cloud-based storage solutions, ensuring data availability, security and alignment with business objectives. |
STMG |
2 - 6 |
Short description of this knowledge area
Security mechanisms relating to larger-scale coordinated distributed systems, including aspects of secure consensus, time, event systems, peer-to-peer systems, clouds, multitenant data centres, & distributed ledgers.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Developing and implementing plans, policies and practices that control, protect and optimise the value and governance of data assets. |
DATM |
2 - 6 |
|
|
Installing, configuring, monitoring, maintaining databases and data stores, ensuring performance and security and adapting to evolving technologies. |
DBAD |
2 - 5 |
|
|
Designing technology infrastructure to meet business requirements, ensuring scalability, reliability, security and alignment with strategic objectives. |
IFDN |
2 - 6 |
|
|
Provisioning, deploying, configuring, operating and optimising technology infrastructure across physical, virtual and cloud-based environments. |
ITOP |
1 - 5 |
|
|
Designing communication networks to meet business requirements, ensuring scalability, reliability, security and alignment with strategic objectives. |
NTDS |
2 - 6 |
|
|
Assessing systems and services to evaluate performance, security, scalability and other non-functional qualities against requirements or expected standards. |
NFTS |
1 - 6 |
|
|
Protecting against and managing risks related to the use, storage and transmission of data and information systems. |
INAS |
2 - 7 |
Short description of this knowledge area
Formal specification, modelling and reasoning about the security of systems, software and protocols, covering the fundamental approaches, techniques and tool support.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Designing systems to meet specified requirements and agreed systems architectures. |
DESN |
2 - 6 |
|
|
Architecting and designing software to meet specified requirements, ensuring adherence to established standards and principles. |
SWDN |
2 - 6 |
|
|
Developing software components to deliver value to stakeholders. |
PROG |
2 - 6 |
|
|
Assessing safety-related software and hardware systems to determine compliance with standards and required levels of safety integrity. |
SFAS |
4 - 6 |
|
|
Applying appropriate methods to assure safety during all lifecycle phases of safety-related systems developments. |
SFEN |
2 - 6 |
Short description of this knowledge area
All aspects of identity management and authentication technologies, and architectures and tools to support authorisation and accountability in both isolated and distributed systems.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Manages identity verification and access permissions within organisational systems and environments. |
IAMT |
1 - 6 |
|
|
Designing systems to meet specified requirements and agreed systems architectures. |
DESN |
2 - 6 |
Short description of this knowledge area
Known categories of programming errors resulting in security bugs, & techniques for avoiding these errors—both through coding practice and improved language design—and tools, techniques, and methods for detection of such errors in existing systems.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Architecting and designing software to meet specified requirements, ensuring adherence to established standards and principles. |
SWDN |
2 - 6 |
|
|
Developing software components to deliver value to stakeholders. |
PROG |
2 - 6 |
|
|
Designing and developing reliable real-time software typically within embedded systems. |
RESD |
2 - 6 |
|
|
Assessing systems and services to evaluate performance, security, scalability and other non-functional qualities against requirements or expected standards. |
NFTS |
1 - 6 |
|
|
Assessing specified or unspecified functional requirements and characteristics of products, systems and services through investigation and testing. |
TEST |
1 - 6 |
|
|
Planning, implementing and controlling activities to integrate system elements, subsystems and interfaces to create operational systems, products or services. |
SINT |
2 - 6 |
|
|
Transitioning software from development to live usage, managing risks and ensuring it works as intended. |
DEPL |
2 - 6 |
|
|
Establishing and deploying an environment for developing, continually improving and securely operating software and systems products and services. |
SLEN |
3 - 7 |
|
|
Designing, building, operationalising, securing and monitoring data pipelines, stores and real-time processing systems for scalable and reliable data management. |
DENG |
2 - 6 |
|
|
Penetration testing |
Testing the effectiveness of security controls by emulating the tools and techniques of likely attackers. |
PENT |
2 - 6 |
|
Leads the adoption, management and optimisation of methods and tools, ensuring effective use and alignment with organisational objectives. |
METL |
2 - 6 |
Short description of this knowledge area
Issues related to web applications and services distributed across devices and frameworks, including the diverse programming paradigms and protection models.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Designing systems to meet specified requirements and agreed systems architectures. |
DESN |
2 - 6 |
|
|
Planning, implementing and controlling activities to integrate system elements, subsystems and interfaces to create operational systems, products or services. |
SINT |
2 - 6 |
|
|
Transitioning software from development to live usage, managing risks and ensuring it works as intended. |
DEPL |
2 - 6 |
Short description of this knowledge area
The application of security software engineering techniques in the whole systems development lifecycle resulting in software that is secure by default.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Establishing and deploying an environment for developing, continually improving and securely operating software and systems products and services. |
SLEN |
3 - 7 |
|
|
Leads the adoption, management and optimisation of methods and tools, ensuring effective use and alignment with organisational objectives. |
METL |
2 - 6 |
|
|
Architecting and designing software to meet specified requirements, ensuring adherence to established standards and principles. |
SWDN |
2 - 6 |
|
|
Designing systems to meet specified requirements and agreed systems architectures. |
DESN |
2 - 6 |
|
|
Planning, implementing and controlling activities to integrate system elements, subsystems and interfaces to create operational systems, products or services. |
SINT |
2 - 6 |
|
|
Transitioning software from development to live usage, managing risks and ensuring it works as intended. |
DEPL |
2 - 6 |
|
|
Planning, identifying, controlling, accounting for and auditing of configuration items (CIs) and their interrelationships. |
CFMG |
2 - 6 |
Short description of this knowledge area
The application of cryptographic algorithms, schemes, and protocols, including issues around implementation, key management, and their use within protocols and systems.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Manages and administers security measures, using tools and intelligence to protect assets, ensuring compliance and operational integrity. |
SCAD |
1 - 6 |
|
|
Manages identity verification and access permissions within organisational systems and environments. |
IAMT |
1 - 6 |
|
|
Protecting against and managing risks related to the use, storage and transmission of data and information systems. |
INAS |
2 - 7 |
|
|
Plans, executes and manages offensive cybersecurity operations, including target selection, electronic target folders and post-operation analysis. |
OCOP |
2 - 6 |
Short description of this knowledge area
Security aspects of networking & telecommunication protocols, including the security of routing, network security elements, and specific cryptographic protocols used for network security.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Designing communication networks to meet business requirements, ensuring scalability, reliability, security and alignment with strategic objectives. |
NTDS |
2 - 6 |
|
|
Providing maintenance and support services for communications networks. |
NTAS |
1 - 5 |
|
|
Protecting against and managing risks related to the use, storage and transmission of data and information systems. |
INAS |
2 - 7 |
Short description of this knowledge area
Security in the design, implementation, & deployment of general-purpose and specialist hardware, including trusted computing technologies and sources of randomness.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Specifying and designing hardware systems and components to meet defined requirements by following agreed design principles and standards. |
HWDE |
2 - 6 |
Short description of this knowledge area
Security challenges in cyber-physical systems, such as the Internet of Things & industrial control systems, attacker models, safe-secure designs, and security of large-scale infrastructures.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
Designing and developing reliable real-time software typically within embedded systems. |
RESD |
2 - 6 |
|
|
Assessing safety-related software and hardware systems to determine compliance with standards and required levels of safety integrity. |
SFAS |
4 - 6 |
|
|
Applying appropriate methods to assure safety during all lifecycle phases of safety-related systems developments. |
SFEN |
2 - 6 |
|
|
Designing technology infrastructure to meet business requirements, ensuring scalability, reliability, security and alignment with strategic objectives. |
IFDN |
2 - 6 |
Short description of this knowledge area
Security concerns and limitations of the physical layer including aspects of radio frequency encodings and transmission techniques, unintended radiation, and interference.
SFIA skills – click links for full skill description including levels
|
SFIA Skill name |
SFIA skill description |
Code |
Levels |
|
|
Designing communication networks to meet business requirements, ensuring scalability, reliability, security and alignment with strategic objectives. |
NTDS |
2 - 6 |
||
|
Designing, installing and maintaining radio frequency based devices and software. |
RFEN |
2 - 6 |
||